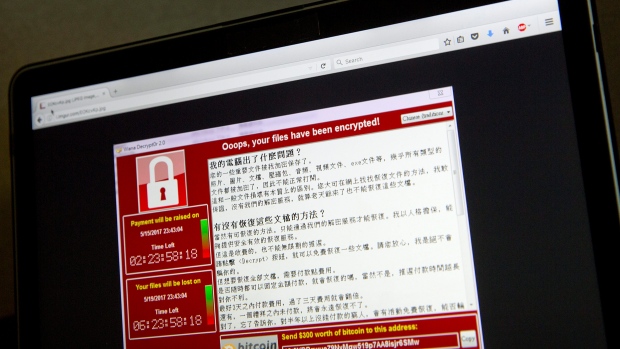
In the wake of a worldwide cyber-attack using WANNACRY ransomware that encrypts Windows systems, cyber security experts say Zimbabwe might see a larger impact on safety and more computers infected when offices open after the weekend break.
As of this writing we have not heard of any organisation being affected by the ransomware.
How does it work?
WannaCry is a form of “ransomware” that locks up the files on your computer and encrypts them in a way that you cannot access them anymore.
The massive global ransomware campaign launched by unknown hackers using NSA tools has affected close to 150 countries.
Ransomware is a program that gets into your computer, either by clicking on the wrong thing or downloading the wrong thing, and then it holds something you need to ransom.
In the case of WannaCry, the malware was circulated by email and it targets were sent an encrypted, compressed file that, once loaded, allowed the ransomware to infiltrate its targets. The program encrypts your files and demands payment in bitcoin in order to regain access.
This ransomware spreads by using a vulnerability in implementations of Server Message Block (SMB) in Windows operating software such as XP, Windows 8 and Windows Server 2003.
A look at how best one can protect oneself from ransomware:
- Maintain updated Antivirus software on all systems
- Check regularly for the integrity of the information stored in the databases
- Regularly check the contents of backup files of databases for any unauthorized encrypted contents of data records or external elements, (backdoors /malicious scripts.)
- Ensure integrity of the codes /scripts being used in database, authentication and sensitive systems
- Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Keep the operating system third party applications (MS office, browsers, browser Plugins) up-to-date with the latest patches.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Don’t open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser
- Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls.
- Disable remote Desktop Connections, employ least-privileged accounts.
- Restrict users’ abilities (permissions) to install and run unwanted software applications.
- Individuals or organizations are not encouraged to pay the ransom, as this does not guarantee files will be released. Report such instances of fraud to CERT-In and Law Enforcement agencies
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsfCarry out vulnerability Assessment and Penetration
- Testing (VAPT) and information security audit of critical networks/systems, especially database servers from CERT-IN empaneled auditors. Repeat audits at regular intervals.
When infected with ransomware and access to unlocking tools please visit https://www.nomoreransom.org/a free online resource developed by Europol, Dutch Police and industry partners. None of the firms targeted indicated whether they had paid or would pay the hackers ransom.